User Administration
FireHydrant works best when your entire incident response team has access to create, update, and manage incidents together. Inviting your team is simple and can be done via the UI. All new users will have Member access. For a primer on FireHydrant's access roles, visit Role-Based Access Controls.
Who should be on FireHydrant?
At FireHydrant, we believe that reliability is a company-wide metric. To that end, FireHydrant is a strong fit for most members of your organization who either respond to incidents or need to be aware of incidents.
We recommend starting with your engineering, SRE, or other teams participating in on-call rotations and responding to incidents. From there, many FireHydrant customers tend to provide access to Support and Success personnel, who often need to communicate incident updates to customers.
Users also provide access to upper leadership who may want access to Analytics and stay in the loop on severe incidents.
Inviting team members
If you have configured SSO, provisioning new users in your IDP will automatically provision team members according to application access. In addition, FireHydrant also supports SCIM for deeper automation and identity management.
The following instructions are for organizations not using SSO and authenticating via email.
-
Go to Settings > Users.
-
Click on the "+ Invite user" button. This takes you to a different page where you can enter the email address of whoever you want to invite to the FireHydrant organization.
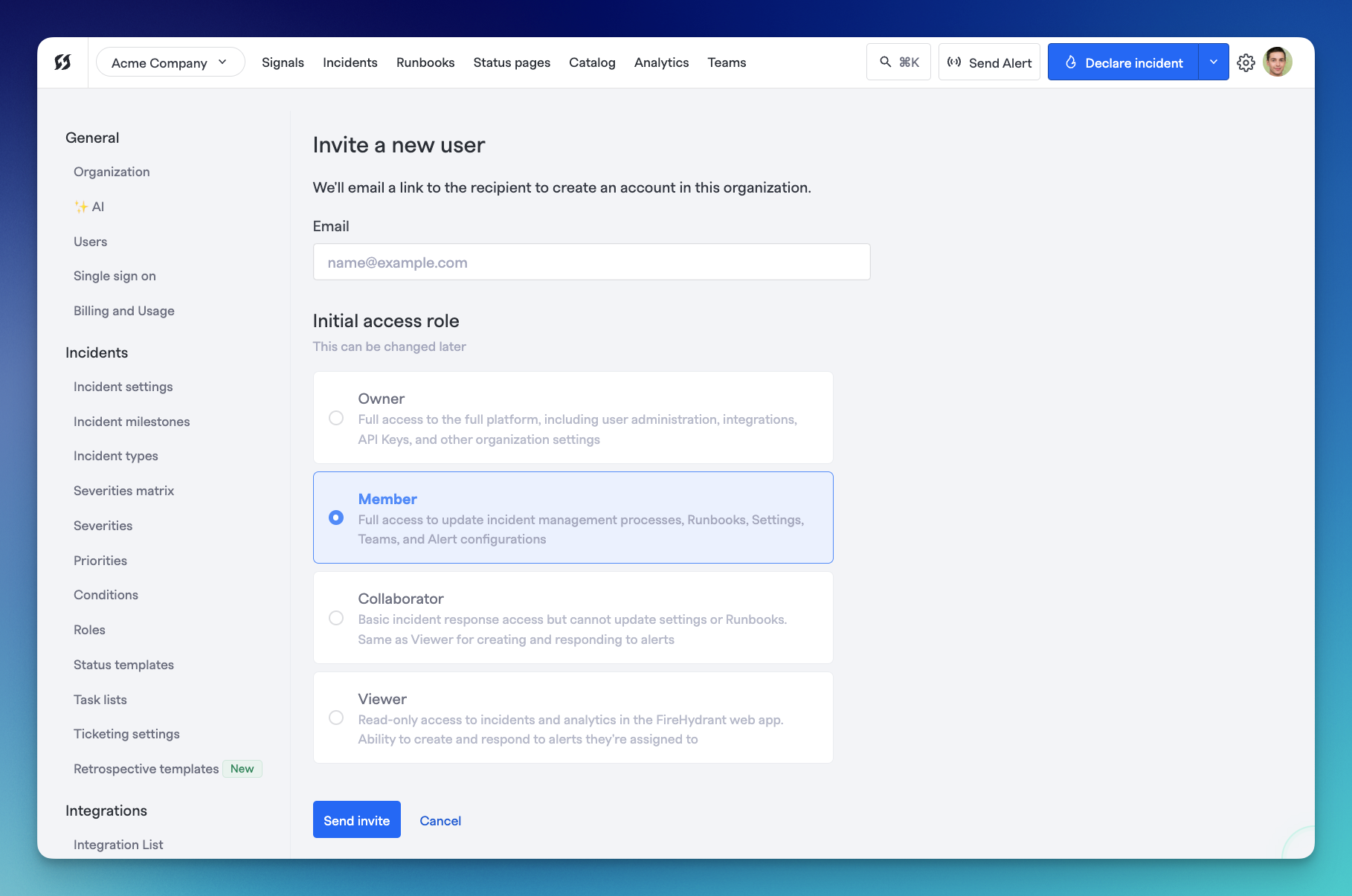
Inviting a user via UI/email
-
Provide the user's email address, select their starting access role, and click Send invite.
- After you invite a user, they'll receive an email invitation.
- When users click Accept My FireHydrant Invitation, they're prompted to provide their name and email, create a password, and accept the privacy policy. Then, they can accept the invitation and join your FireHydrant organization.
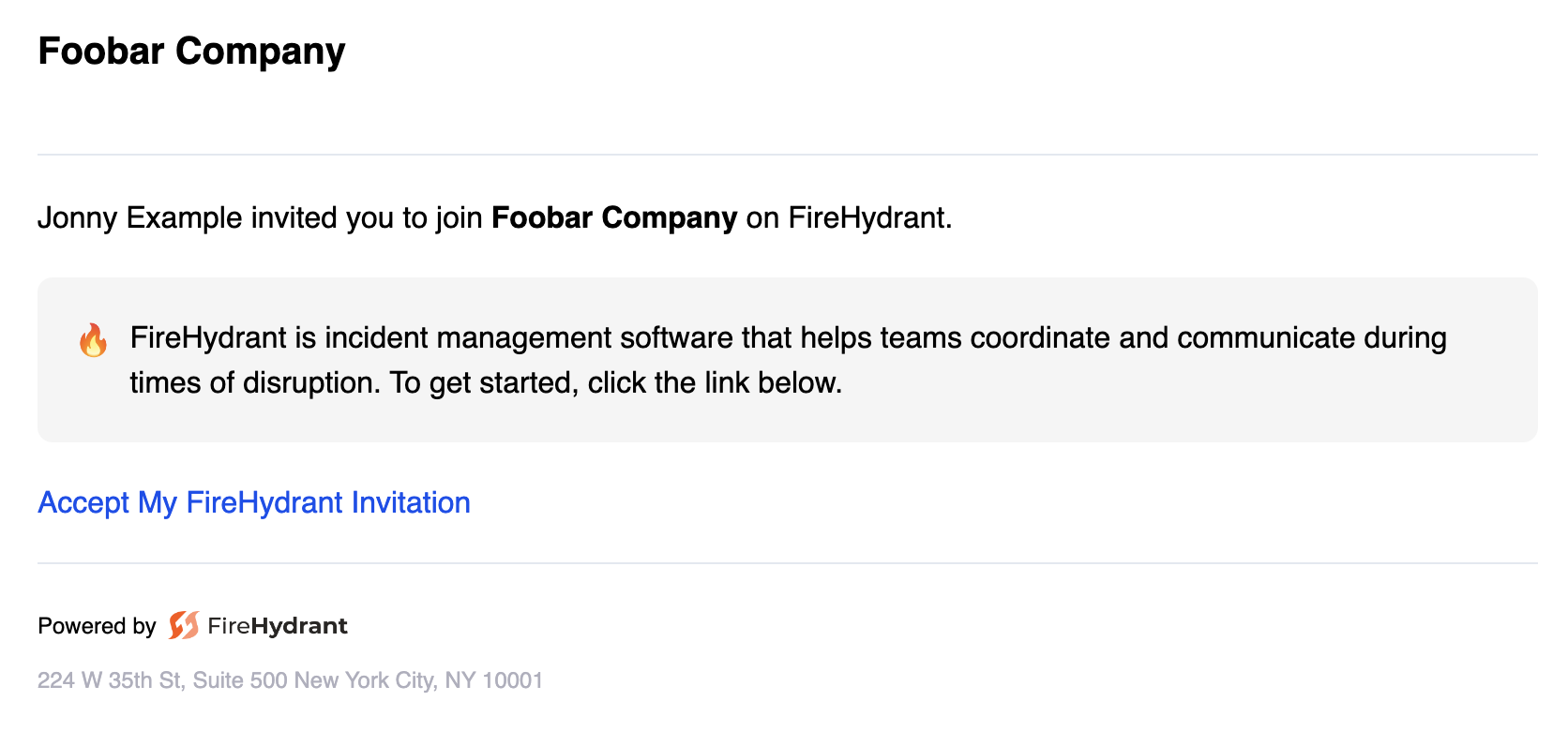
Example invitation email
Note:Make sure your team members accept your email invitation instead of signing up separately on the website. Signing up on the website creates a new organization and account. FireHydrant enforces unique email addresses system-wide, so if someone accidentally registers on their own, they will need to reach out to Support to disable the duplicate account/email before they can accept your invitation.
Manually Disable a FireHydrant User
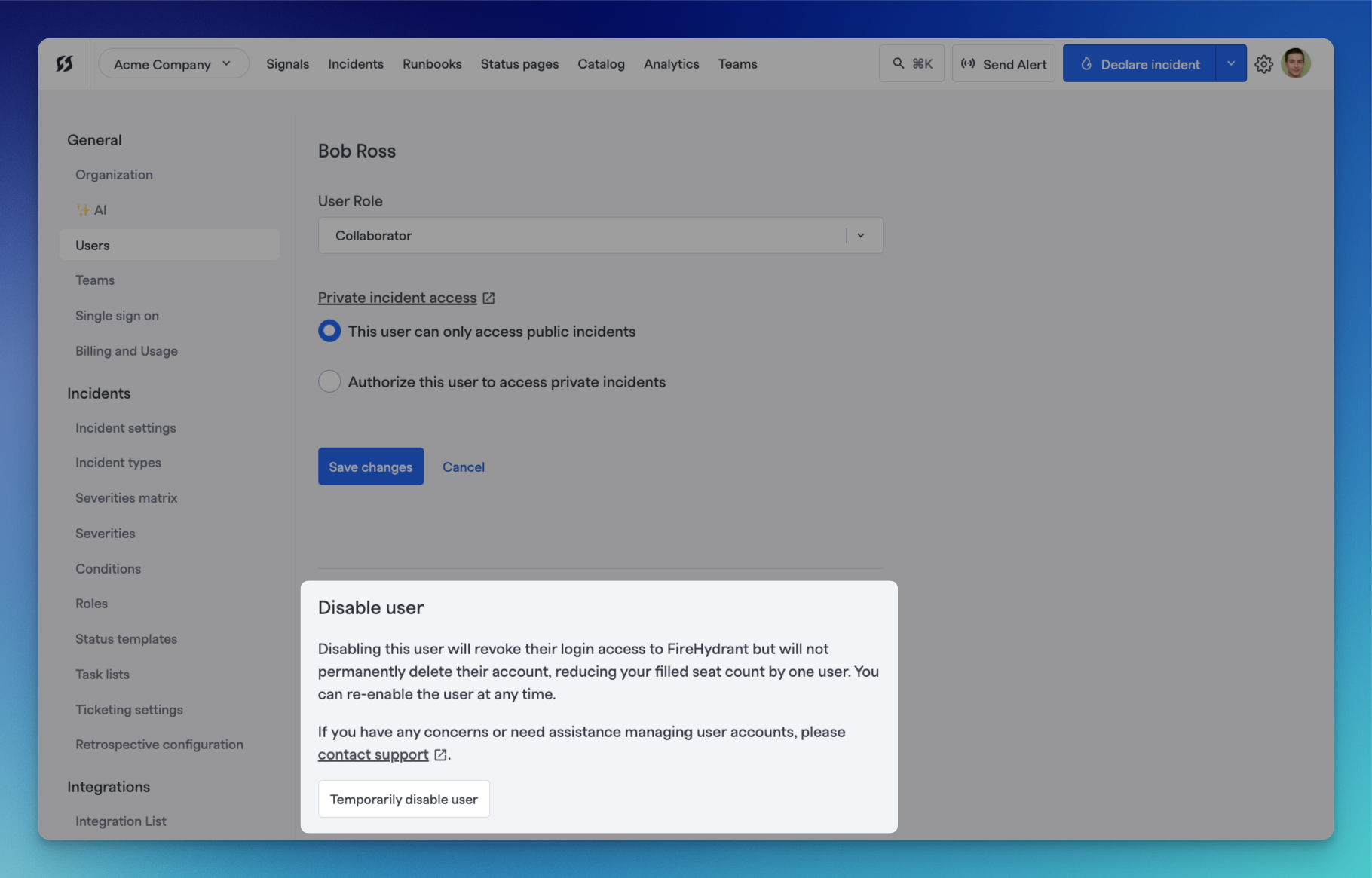
Disabling a user via web UI
Sometimes, teammates move on or change roles, and you want to ensure they can no longer access FireHydrant. You can automate deprovisioning if you are using SCIM Configuration. If not, then aside from reaching out to support, you can also do this yourself in the UI (requiresOwner permissions).
- Navigate to Settings> Users and locate the user you want to disable.
- Click on the user, and scroll down to the "Disable user" section of the individual user details page. You can then choose to disable by selecting "Temporarily disable user." This is a reversible action, so have no fear! Disable away.
Filtering Users List
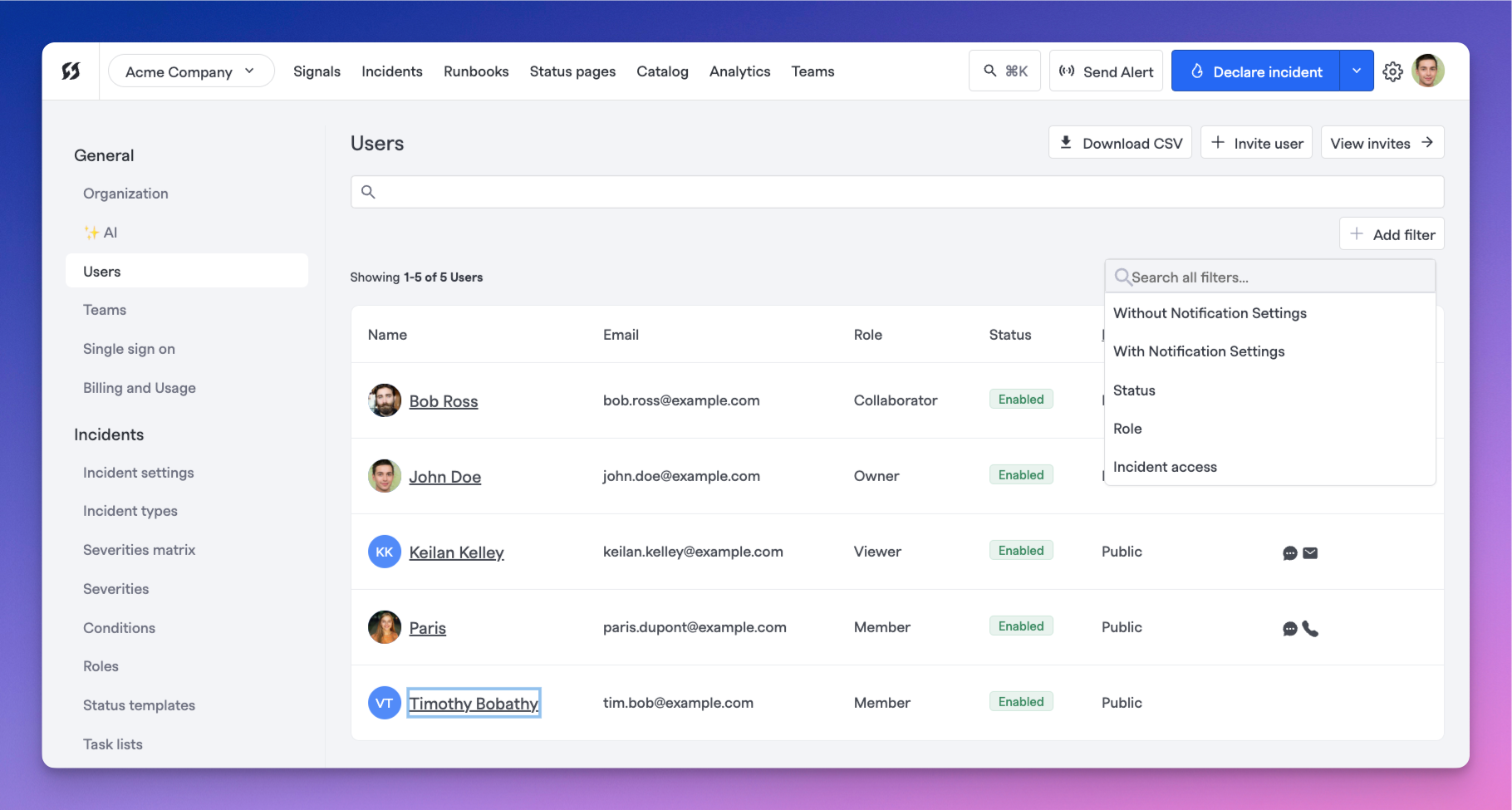
Users page with filters expanded
On the Users page, you can search for specific users and filter users by a few different parameters.
-
Navigate to Settings> Users.
-
Click on the Filter users dropdown or type into the search bar and hit 'Enter' to filter and search.
FireHydrant supports the following filters for showing users:
- Without Notification Settings - Shows users who do not have the specified notification method(s) configured
- With Notification Settings - Shows users who have the specified notification method(s) configured
- Status - Shows users who are enabled/disabled. By default, the interface only shows active/enabled users
- Role - Shows users with the specified access roles
- Incident access - Shows users with public/private/both incident access
Automating User Administration
We recommend automating user provisioning and de-provisioning with SSO and SCIM when possible, as most enterprise companies will use an IDP to manage access to all of their applications.
In addition, FireHydrant does provide direct APIs to manage users via SCIM, in case you do not use an IDP but still want to manage users programmatically.
Next Steps
- As mentioned above, look at our SSO and SCIM docs or the API to see how you can automate FireHydrant account provisioning as part of your IDP workflows
- Read about Role-Based Access Controls on FireHydrant and how to assign the right roles for your users
- Learn more about Team Management as well as how to assign users and teams to incidents
Updated 6 months ago
