Okta for Status Pages
With FireHydrant's status pages, you can lock them behind your SSO provider so that only employees or other organization members can access them.
Note:We currently only support OIDC for SSO-authenticated status pages. In addition, this limits access to anyone in your organization who can login via SSO, not only users with FireHydrant licenses.
1. Create Status Page
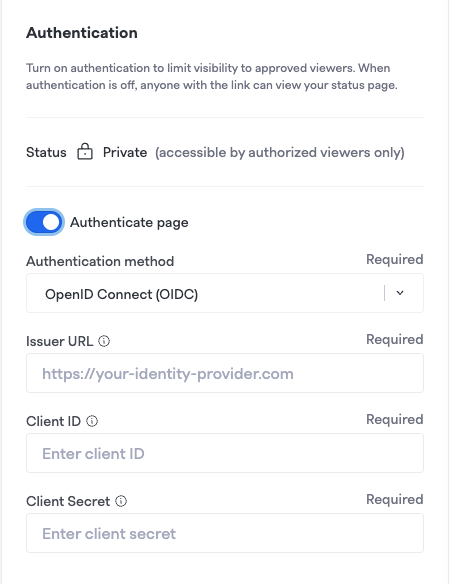
You'll first want to set up and configure a status page. Once you are on the final "Authentication" step, toggle "Authenticate page" and you can start working through these instructions to lock it behind authentication.
2. Create Okta OIDC Application
Reference documentation here: https://help.okta.com/en-us/content/topics/apps/apps_app_integration_wizard_oidc.htm
-
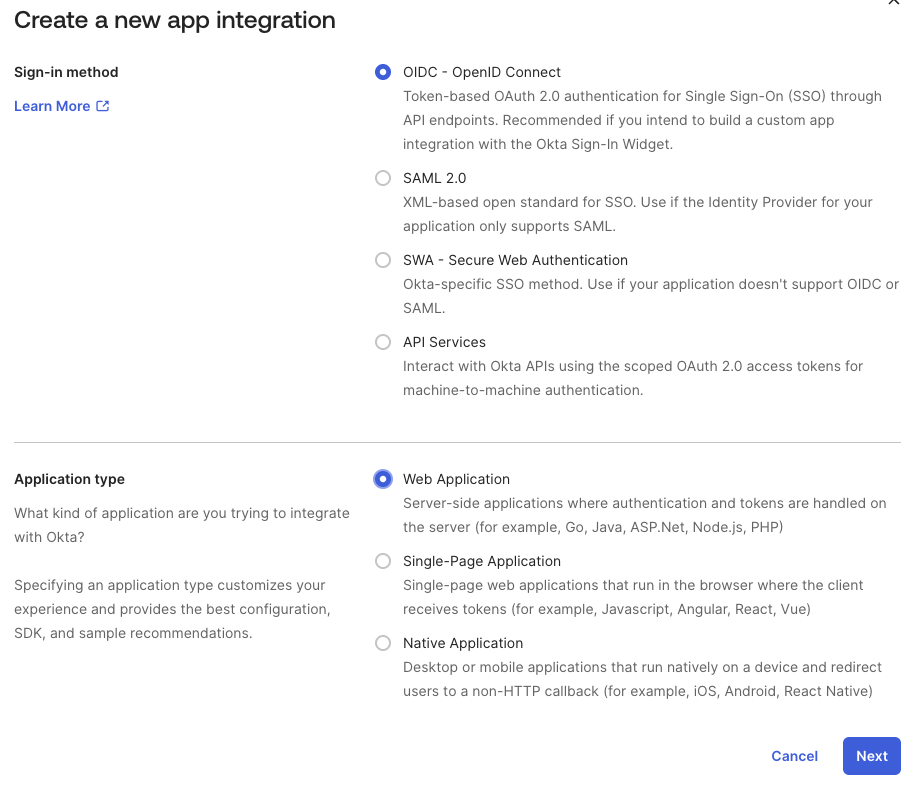
In Applications, click Create App Integration. On the popup that follows, choose OIDC - OpenID Connect as the sign in method and Web Application as the Application Type. Then click next.
-
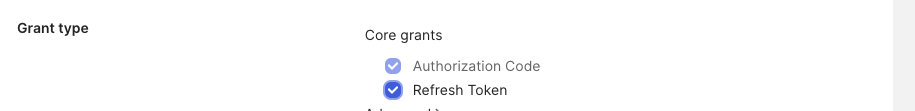
On the next screen, under General Settings, click the checkbox to add the Refresh Token grant type.
-
In the Sign-in redirect URIs section, add
https://<statuspage hostname>/oauth2/callbackwhere<statuspage hostname>is the DNS name you chose when creating your status page.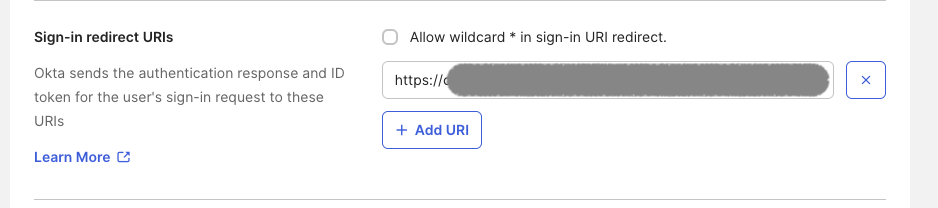
-
Remove any URI in the Sign-out redirect URIs section.
-
Your admin can choose to assign all users or only a limited set, based on your business needs. Once this is complete, click Save.
3. Complete Configuration
Once this is complete, you’ll need to gather 3 pieces of information to add authentication to your status page:
-
Issuer URL - This will be your okta domain. For example:
https://mycompany.okta.com -
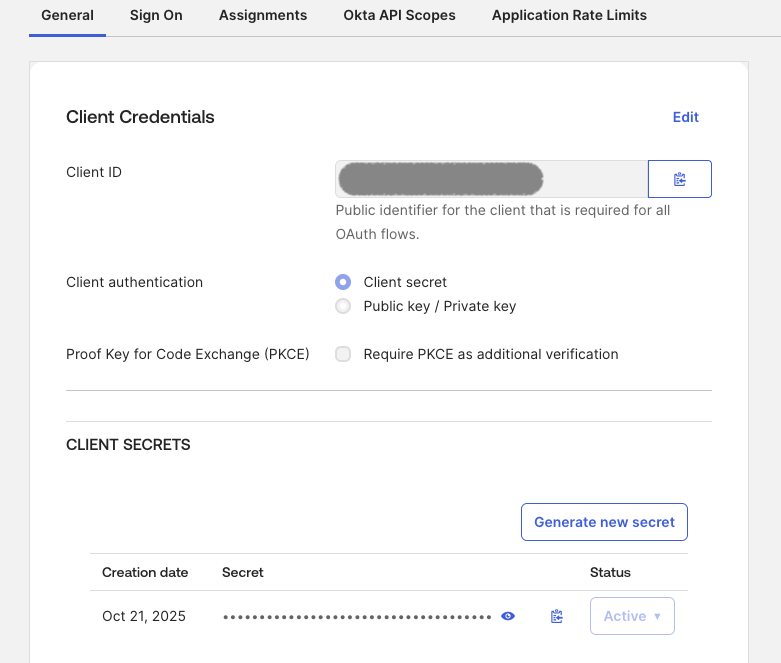
Client ID - This is in the general tab for the application you just created in the Client Credentials section.
-
Client Secret - This is in the general tab for the application you just created in the Client Secrets section. It is hidden by default and you can click the Copy To Clipboard or Reveal buttons to get it.
4. Publish and Verify
Once the Status Page is showing as verified on the Status Page overview, publish your new status page! When you attempt to access an SSO-locked status page, you should be redirected to your organization's SSO sign-on page.

Next Steps
- Learn how to use your FireHydrant status page
- Learn more about Posting Updates during incidents
Updated about 2 months ago
