Kubernetes
FireHydrant's Kubernetes integration allows you to send updates about the workloads deployed in your clusters automatically to FireHydrant. This lets you follow the lifecycle of a change, from GitHub pull request to pod deployment.
Resources Tracked:
- DaemonSet
- Deployments
- ReplicaSet
- Services
- StatefulSets
Prerequisites
- You will need Owner permissions in FireHydrant to generate API keys
- You will need access to your infrastructure to deploy a Kubernetes manifest.
Installation Instructions
The integration works by spinning up a FireHydrant worker in your cluster that sends updates and calls back to FireHydrant.
You will need an API key for the controller to use for authentication. We recommend creating an API key specifically for this integration. This token goes in the firehydrant-keys Kubernetes secret. See an example manifest file below.
Note:Be sure to change
'YOUR_BOT_TOKEN'and'YOUR_ENVIRONMENT_NAME'before deploying the manifests.
apiVersion: v1
kind: Namespace
metadata:
name: firehydrant-system
---
apiVersion: v1
kind: Secret
metadata:
name: firehydrant-keys
namespace: firehydrant-system
stringData:
FIREHYDRANT_API_KEY: 'YOUR_BOT_TOKEN'
---
kind: ConfigMap
apiVersion: v1
metadata:
name: firehydrant-cm
namespace: firehydrant-system
data:
config.yml: |
apiToken: '$FIREHYDRANT_API_KEY'
fireHydrantUrl: 'api.firehydrant.io'
watch:
- namespace: "*"
environment: 'YOUR_ENVIRONMENT_NAME'
resources:
- resource: deployments.v1.apps
updateOn: ["spec", "metadata"]
includeDiff: true
skipServiceCreate: false
- resource: configmaps
updateOn: ["data"]
includeDiff: true
skipServiceCreate: true
---
apiVersion: v1
kind: ServiceAccount
metadata:
name: firehydrant-k8s-changelog-serviceaccount
namespace: firehydrant-system
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: firehydrant-system-clusterrole
rules:
- apiGroups:
- ""
- "extensions"
- "apps"
resources:
- configmaps
- services
- deployments
- replicasets
- daemonsets
- statefulsets
verbs:
- list
- watch
- get
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: firehydrant-clusterrole-nisa-binding
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: firehydrant-system-clusterrole
subjects:
- kind: ServiceAccount
name: firehydrant-k8s-changelog-serviceaccount
namespace: firehydrant-system
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: firehydrant-k8s-changelog
namespace: firehydrant-system
labels:
app: firehydrant-k8s-changelog
app.kubernetes.io/name: firehydrant-k8s-changelog
app.kubernetes.io/component: changelog
spec:
replicas: 1
strategy:
type: RollingUpdate
selector:
matchLabels:
app: firehydrant-k8s-changelog
template:
metadata:
labels:
app: firehydrant-k8s-changelog
spec:
serviceAccount: firehydrant-k8s-changelog-serviceaccount
containers:
- name: changelog
image: quay.io/firehydrant/k8s-changelog:v0.0.20
command:
- firehydrant-k8s-changelog
- watch
envFrom:
- secretRef:
name: firehydrant-keys
volumeMounts:
- name: config
mountPath: /etc/k8s-watcher
resources:
limits:
cpu: 10m
memory: 128Mi
requests:
cpu: 10m
memory: 128Mi
volumes:
- name: config
configMap:
name: firehydrant-cmAfter this is deployed, any changes made to your clusters will automatically be logged in FireHydrant's change events:
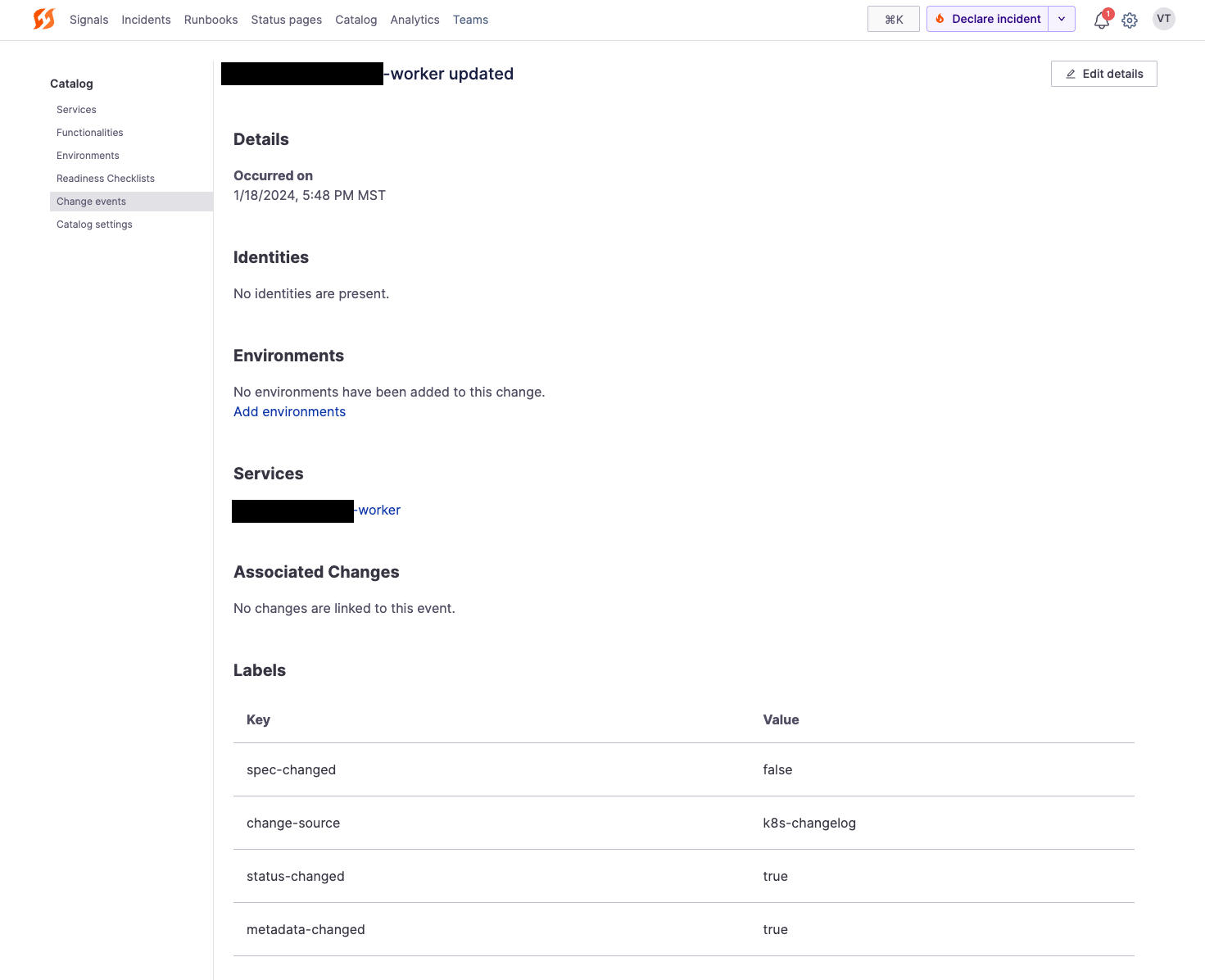
Example change event from Kubernetes
In addition, FireHydrant will automatically add new services/pods in your Kubernetes cluster to FireHydrant's Service Catalog as well as the ENVIRONMENT you specify above if it doesn't already exist.
Next Steps
- Learn more about Change Events
- See how FireHydrant's Service Catalog helps your team assemble more quickly and log service incident metrics
- Browse the rest of our integrations
Updated 12 days ago
