Role-Based Access Controls (RBAC)
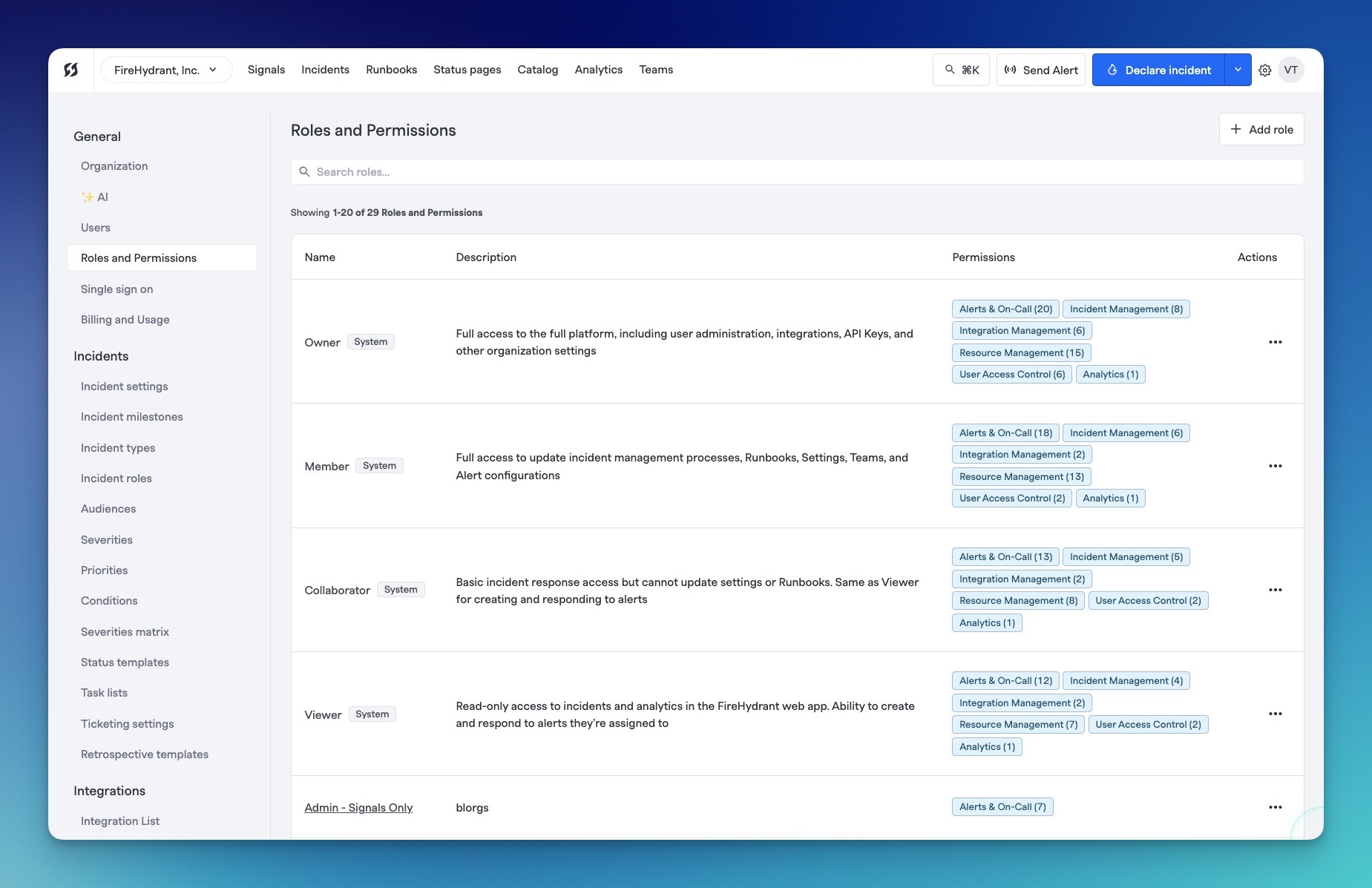
User roles in FireHydrant
FireHydrant offers user roles to help restrict and define access to parts of the platform, enabling you to create a secure and scalable incident management process.
Users, Roles, and Definitions
Licensed vs. Unlicensed users
- Licensed users - Users with FireHydrant accounts and login access, split into 4 access roles (see next section)
- Unlicensed users - Everyone else. Users who cannot log in and perform the vast majority of actions with one exception.
Any user in Slack or Microsoft Teams, including unlicensed, can still join incident channels/chats, keep tabs on an open incident, and participate in conversations within those channels. However, unlicensed users can't take any actions that change the incident state, such as running most commands, posting updates, assigning/completing tasks, being assigned roles, etc.
Depending on your settings, Unlicensed users can perform a set of basic essential tasks from integrated chat applications like Slack or MS Teams:
- Declare incidents (can be configured in Integration settings)
- Page and Lookup On-Call (Slack only)
- ...and more
For full details, visit the command docs pages for Slack and Microsoft Teams.
Access Roles vs. Incident Roles
Access roles (this page) are for determining user access to different features and capabilities on the FireHydrant platform. These should not be confused with Incident Roles, which are titles provided to specific users on incidents and can change what tasks are assigned to them and impact other automations in Runbooks.
Organization vs. Team-Level Permissions
FireHydrant allows you to customize permissions both at an organization level (access roles) as well as within a team (called Team-Level Permissions). Certain permissions at the organization level will override team-level permissions (e.g., access roles with Manage Teams permission can manage and modify members and settings on any of the teams), but within a team, users can be given permissions to modify team-only items like schedules, policies, team membership, and more.
Access Roles, custom or out-of-box, are defined at the organization level. For more information about team-level permissions, see Team-Level Permissions below.
Predefined Access Roles
FireHydrant offers four access roles out-of-box. Any modifications or other desired behaviors should be done via Custom Access Roles.
- Owner: Full access to the full platform, including user administration, integrations, API Keys, and other organization settings
- Member: Full access to update incident management processes, Runbooks, Settings, Teams, and Alert configurations
- Collaborator: Basic incident response access but cannot update settings or Runbooks. Same as Viewer for creating and responding to alerts if assigned
- Viewer: Read-only access to incidents and analytics in the FireHydrant web app. Ability to create and respond to alerts if they're assigned
- Unlicensed: Not a custom access role, but included to visually demonstrate what people without FireHydrant accounts can do.
Alerts & On-Call Permissions
Note that users may have Viewer role permissions but can still be on-call and respond to pages.
| Action | Owner | Member | Collaborator | Viewer |
|---|---|---|---|---|
| Create Alerts and Page Others | ✅ | ✅ | ✅ | ✅ |
| Request Coverage for Shifts, Claim Shifts | ✅ | ✅ | ✅ | ✅ |
| Respond to Alerts^ | ✅ | ✅ | ✅ | ✅ |
| Read Alerts | ✅ | ✅ | ✅ | ✅ |
| Read Alert Grouping | ✅ | ✅ | ✅ | ✅ |
| Read Alert Rules/Triggers | ✅ | ✅ | ✅ | ✅ |
| Read Call Routes | ✅ | ✅ | ✅ | ✅ |
| Read Escalation Policies | ✅ | ✅ | ✅ | ✅ |
| Read Event Sources | ✅ | ✅ | ✅ | ✅ |
| Read On-Call Schedules & Shifts | ✅ | ✅ | ✅ | ✅ |
| Read Team Support Hours | ✅ | ✅ | ✅ | ✅ |
| Read Webhook Alert Targets | ✅ | ✅ | ✅ | ✅ |
| Manage Personal Notification Preferences | ✅ | ✅ | ✅ | ✅ |
| Manage On-Call Shifts/Shift Overrides | ✅ | ✅ | ✅ | |
| Manage Alert Grouping | ✅ | ✅ | ||
| Manage Alert Rules/Triggers | ✅ | ✅ | ||
| Manage Call Routes | ✅ | ✅ | ||
| Manage Escalation Policies | ✅ | ✅ | ||
| Manage Event Sources | ✅ | ✅ | ||
| Manage On-Call Schedules | ✅ | ✅ | ||
| Manage Team Support Hours | ✅ | ✅ | ||
| Manage Webhook Alert Targets | ✅ | ✅ | ||
| Read Global Notification Policy Compliance | ✅ | |||
| Manage Global Notification Policy | ✅ |
^Note:
Users will always be able to interact with alerts that are targeted at them, even if they don't have explicit "Respond to Alerts" permission.
Analytics Permissions
| Action | Owner | Member | Collaborator | Viewer |
|---|---|---|---|---|
| Read Analytics | ✅ | ✅ | ✅ | ✅ |
Incident Management Permissions
| Action | Owner | Member | Collaborator | Viewer |
|---|---|---|---|---|
| Create Incidents (manually or from alerts) | ✅ | ✅ | ✅ | ✅ |
| Invited to Slack incident channels | ✅ | ✅ | ✅ | ✅ |
| Read Incidents (including via Tabs in MS Teams) | ✅ | ✅ | ✅ | ✅ |
| Read Incident Settings | ✅ | ✅ | ✅ | ✅ |
| Read Status Templates | ✅ | ✅ | ✅ | ✅ |
| Run General Slack Commands | ✅ | ✅ | ✅ | ✅ |
| View Internal and External Status Pages | ✅ | ✅ | ✅ | ✅ |
| Respond to Incidents | ||||
| ↳ Assigned Incident Roles | ✅ | ✅ | ✅ | |
| ↳ Assigned Tasks and Follow-Ups | ✅ | ✅ | ✅ | |
| ↳ Attach/Execute Runbooks | ✅ | ✅ | ✅ | |
| ↳ Manage Incidents in the web application, Slack, or Microsoft Teams | ✅ | ✅ | ✅ | |
| ↳ Manage and Edit External Status Page Updates | ✅ | ✅ | ✅ | |
| ↳ Participate in Retrospectives | ✅ | ✅ | ✅ | |
| ↳ Post Incident Updates (not including to external status pages) | ✅ | ✅ | ✅ | |
| ↳ Run most Slack Commands or Microsoft Teams Commands, with some exceptions (see the docs) | ✅ | ✅ | ✅ | |
| ↳ Star Events or Other Incident Timeline Actions | ✅ | ✅ | ✅ | |
| Manage Incident Settings | ✅ | ✅ | ||
| Read Private Incidents** | ✅ | |||
| Manage Status Templates | ✅ |
**Note:
Users without private incident access (all-encompassing) can be added to individual private incidents ad-hoc by people who have access. This permission only allows viewing/accessing Private Incidents - in order to respond to Private Incidents, you will also need the
Manage Incidentspermissions above.For more information, see Private Incidents.
Integration Management Permissions
| Action | Owner | Member | Collaborator | Viewer |
|---|---|---|---|---|
| Read Integrations | ✅ | ✅ | ✅ | ✅ |
| Read Webhooks | ✅ | ✅ | ✅ | ✅ |
| Read Secrets | ✅ | |||
| Manage Integrations | ✅ | |||
| Manage Secrets | ✅ | |||
| Manage Webhooks | ✅ |
Resource Management Permissions
| Action | Owner | Member | Collaborator | Viewer |
|---|---|---|---|---|
| Read Audiences | ✅ | ✅ | ✅ | ✅ |
| Read Change Events | ✅ | ✅ | ✅ | ✅ |
| Read Organization Settings | ✅ | ✅ | ✅ | ✅ |
| Read Runbooks | ✅ | ✅ | ✅ | ✅ |
| Read Service Catalog | ✅ | ✅ | ✅ | ✅ |
| Read Teams | ✅ | ✅ | ✅ | ✅ |
| Manage Audiences | ✅ | ✅ | ||
| Manage Change Events | ✅ | ✅ | ||
| Manage Runbooks | ✅ | ✅ | ||
| Manage Service Catalog | ✅ | ✅ | ||
| Manage Teams | ✅ | ✅ | ||
| Manage Organization Settings | ✅ | |||
| Read Audit Logs | ✅ |
User Access Control Permissions
Custom Access Roles
Any Owner or access role with Manage Roles & Permissions can navigate to the Roles & Permissions page and create/make changes to custom access roles.
In addition, any Owner or access role with Manage Users permission can navigate to the Users page and update another user's access role. The exception to this is that users cannot update their own roles if they're not Owners - they must request another user with adequate permissions to modify their assigned access role.
Additionally, you can update user roles using our SCIM API and your IDP (Okta, Active Directory, etc.). Read our SCIM Configuration docs to learn about provisioning users and roles.
Creating a Custom Role
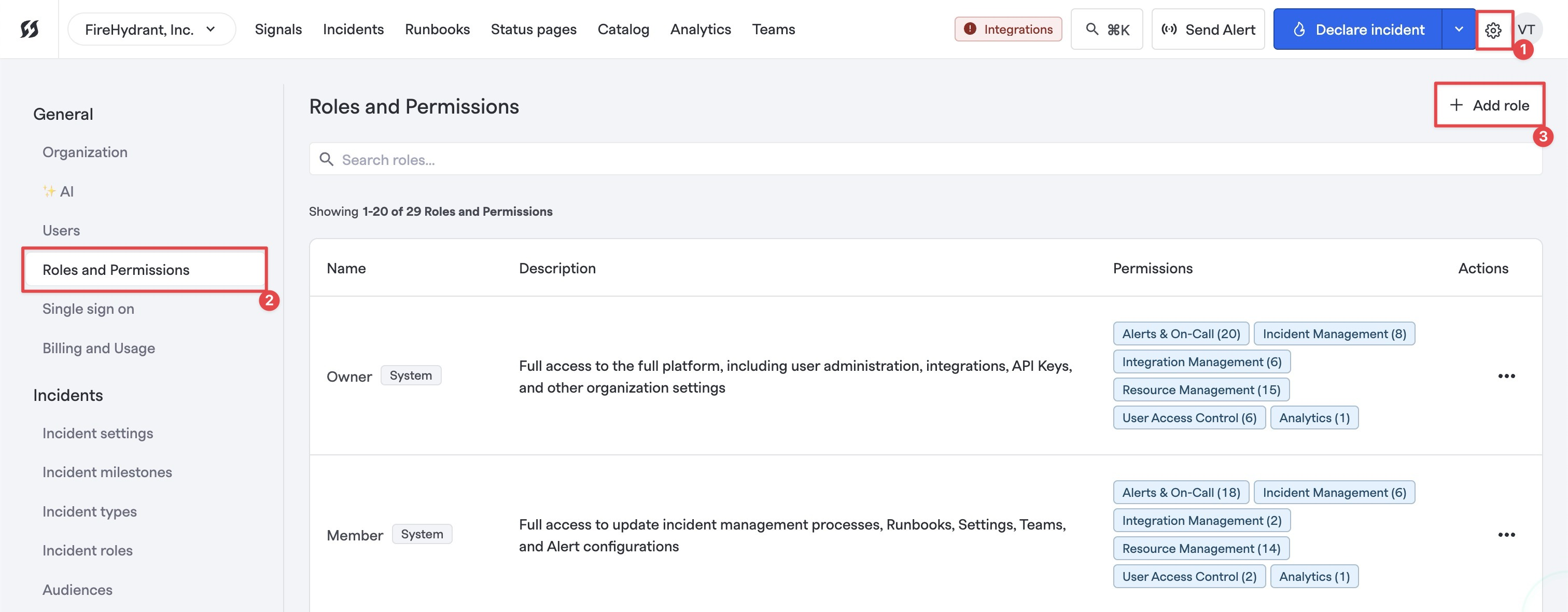
Adding a custom access role
- Navigate to Settings > Roles & Permissions and then click on "+ Add role."
- On this next page, supply a Name and Description for this custom role you're creating.
- Below on the same page, you can select the permissions you would like this particular role to have. The full list of selectable permissions can be browsed below.
- NOTE: Certain permissions will require and automatically check other prerequisite permissions/dependencies. For example, to fully read incidents, the user must also have read access to several other objects like teams and alerts. You'll receive a popup notification stating what additional permissions will be checked, if any.
- Once configured, click "Create role" at the top right.
- Remember to go to Settings > Users and assign your new custom role to one or more users in order to set and customize their permissions.
On the role creation page, you also have some utility buttons:
- Deselect all will uncheck all boxes
- Select all will check all boxes
- Reset will revert the selections back to their last saved state. If editing a role, it reverts permissions to their prior state, and if creating a new role, it does the same thing as Clear.
Team-Level Permissions
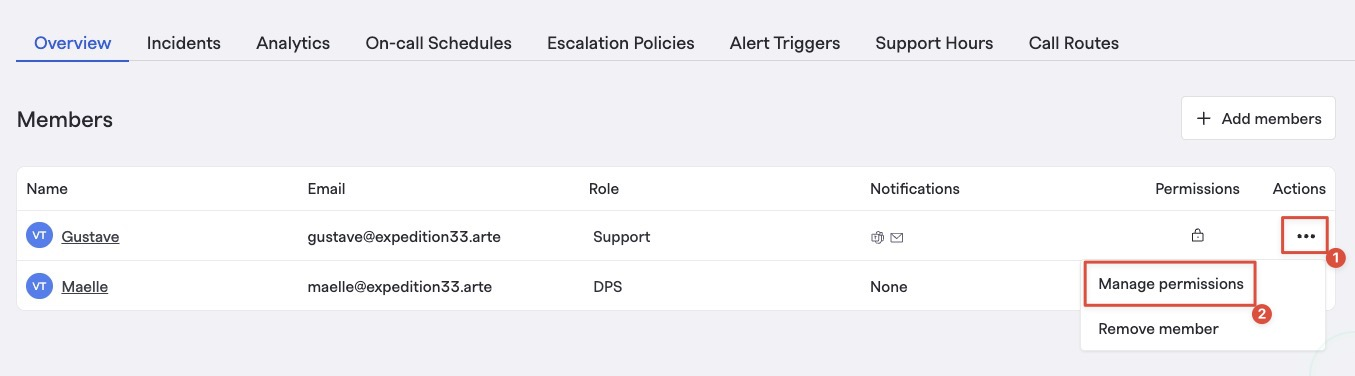
Managing individual team members' permissions
In addition to organization-level access roles, teams can lock down configurations for their teams. This will federate permissions for each team member to modify specific resources within the team, even if they don't have permissions broadly across the org to do the same (e.g., they can manage Users within the team, but they cannot broadly manage Users in the organization).
These permissions can be found by clicking on the ellipses next to each member in the members list.
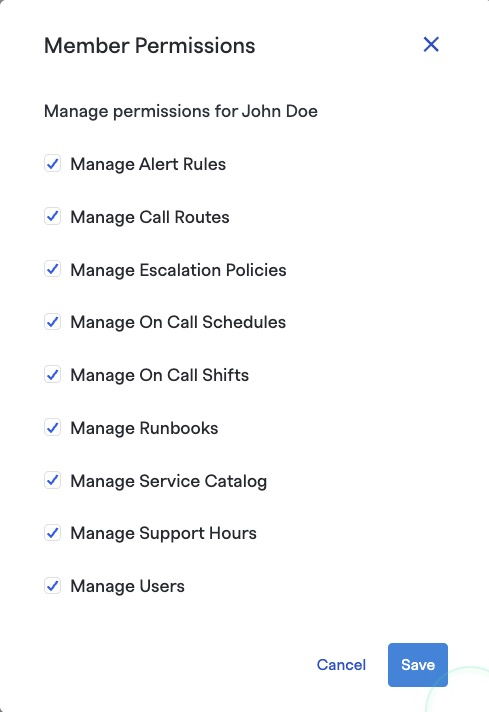
Team-level permissions
Runbooks and Service Catalog components can have assigned Owning Teams, which prevents non-team members from modifying or managing those resources once assigned. Team-level permissions, in these cases, will take precedence over org-level permissions.
For example, let's say Service A is owned by Team A, User X is part of the team, and User X doesn't have Manage Service permissions within the team. At this point, it doesn't matter if the user's assigned organization role has Manage Service permissions - they will not be able to edit Service A. See the following graphic for a visual representation:
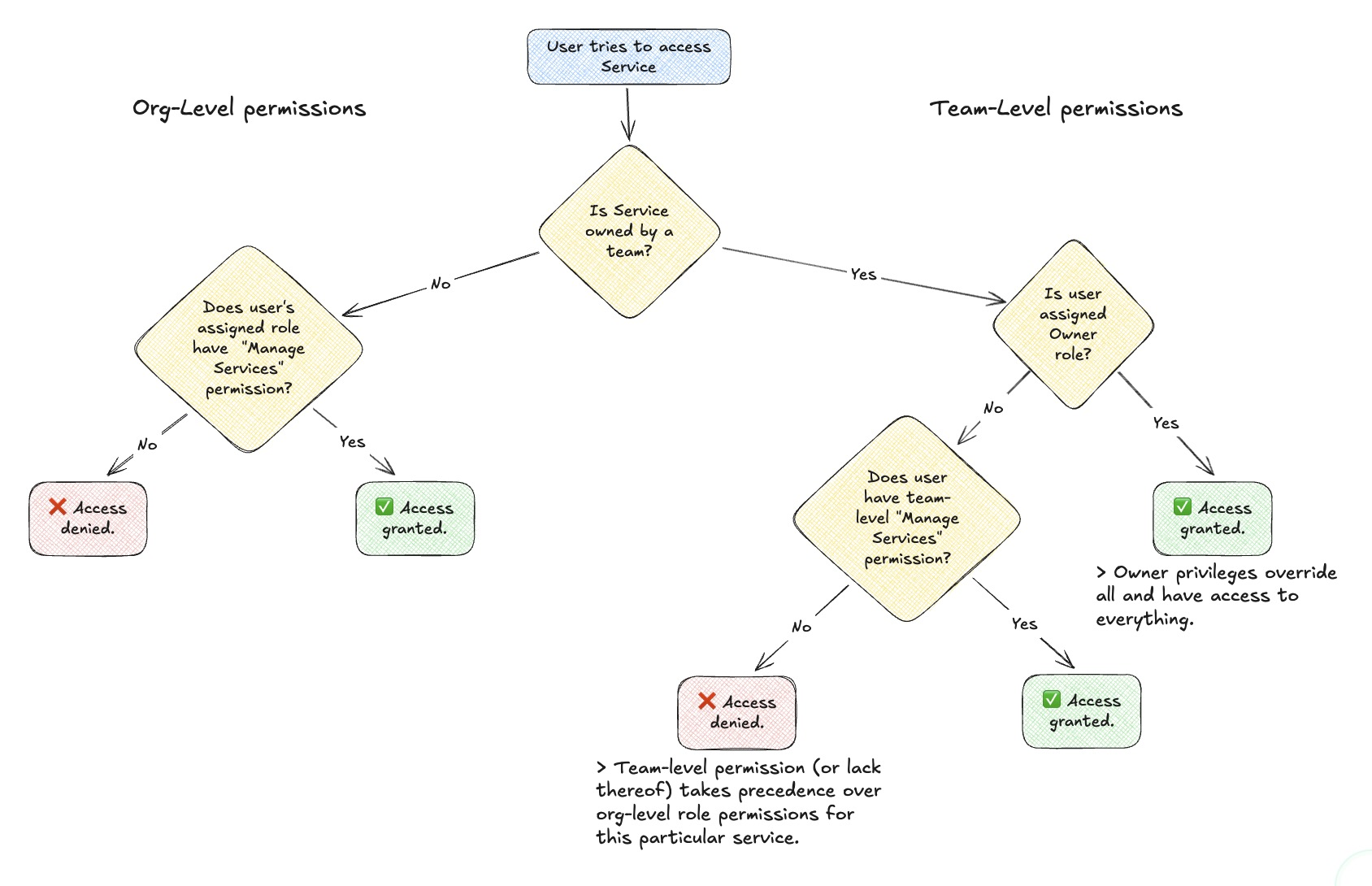
Flowchart of permissions precedence
For Signals-specific features (Alert Rules, Schedules, Policies, etc.), see the next subsection.
Note:
Team-level permissions override org-level permissions, with only one exception. In other words:
- If Service A or Runbook A are owned by Team A, then nobody outside of Team A can modify that service or runbook even if they have
Manage Service CatalogorManage Runbookspermissions assigned to their org-level role.- If Team A has chosen to lock down its Signals settings, then even users with
Manage Escalation Policiespermission at the organization level cannot edit Team A's escalation policies.The exception to this is for users with Owner access role. Owners can be thought of as superadmins with access to everything.
Signals-Specific Feature Permissions
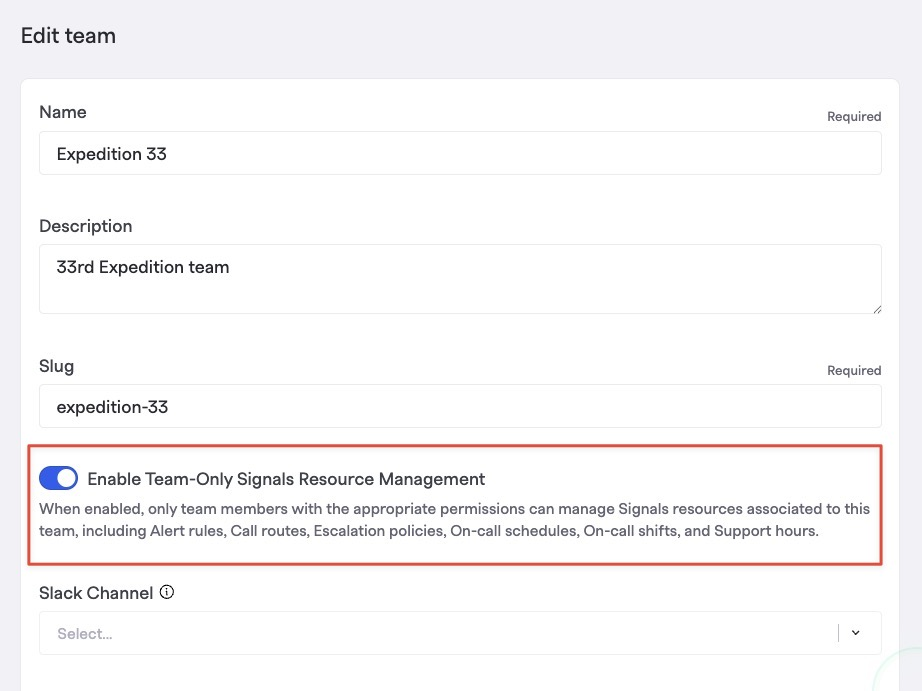
Restricting the modification of a team's Signals configurations to only within the team
To maintain existing behavior for customers, FireHydrant has not automatically locked down permissions for Signals configurations by team to prevent a sudden loss of editing permissions from existing users.
To enable the behavior, go into a Team's settings and enable this switch for Enable Team-Only Signals Resource Management. As soon as this setting is enabled, only users who are explicitly on the membership list of this team will be allowed to modify any Signals-related config on the team (e.g., Schedules, Policies, etc.), and only if they have the team-level permission required to do so.
Frequently asked questions
I want to make sure users can only modify their own team's settings. How do I achieve this?
- First, ensure that a user does not have Owner permissions, as Owners can modify all configurations on any team.
- Users assigned
Manage Teamspermissions at the organization level can modify Team details, settings, and memberships across all teams. If you don't want this, make sure that a user only hasRead Teamspermission. - Then, make sure that the individuals on the team have the team-level permissions enabled for anything you want them to be able to manage.
This flow is useful for configuring e.g., Team Leads, who can manage their own teams but not other teams.
Can an unlicensed user access incident retrospectives?
FireHydrant's incidents and retrospectives are a part of the web application and require a license to access. Retrospectives can be exported as PDF or supported integrations like Confluence and Google Docs to be shared broadly.
For more information, visit Preview & Export Retrospectives.
Can a Viewer or non-licensed user “star” events to be included in the export timeline?
Starring events is considered a state-altering action, and subsequently is not available for the default Viewer role or anyone without Manage Incidents permission.
If a Viewer or unlicensed user posts chat messages into the incident Slack or Microsoft Teams channel, will those still be recorded by FireHydrant into the timeline
Yes, all messages in incident channels are recorded in the incident timeline regardless of who they're from.
Can a Viewer or non-licensed user be assigned action-items?
Users must at least have Manage Incidents permissions or be Collaborator+ (of the out-of-box roles).
Can a non-licensed user view a status page?
Yes. You do not need to be a licensed user on FireHydrant to view a status page.
Updated 4 days ago
